Filter

02.01.2023
Copyright Infringement Music
Unauthorised Use of Music at Fashion Event - a Real Damage Event
It’s complicated: This sentence really sums up the regulations for the commercial use of music well. An IT service provider insured by exali really got a taste of this in this real damage event.

30.12.2022
exali Annual Review: Damage Events
Damage Events of 2022 That We Will Remember
Missing documents, Trojans and fake CEOs: This isn’t the plot of a film but our 2022 annual review of damage events!

23.12.2022
2022 Review: The Most Important Articles on IT Topics
Cybercrime and Digital Nomads: The IT Topics of 2022
Why cybersecurity is becoming more and more important, what damage events happened to IT service providers in 2022 and why digital nomads are on the rise: We’ve summed up these and other topics in our IT review.

16.12.2022
Is Mastodon the New Twitter?
Mastodon: How the Social Network Works
Tooting instead of Tweeting: Mastodon works differently from Twitter and other social networks in many ways. In this article, we tell you how the Fediverse works, who can benefit from it, and what you should consider.

12.12.2022
Trademark Protection Becomes a PR Disaster
Lego versus YouTuber: How a Trademark Lawsuit Alienated Loyal Fans
Lego takes rigorous action against trademark infringement, including against enthusiastic Lego fans and successful YouTubers. Why Lego doesn’t have much choice and why we may soon have to say click bricks instead of Lego...

05.12.2022
Business Risks of Advertising Agencies
Watch Out for Written Warnings: 10,000 Euros for Errors in Advertising
An SUV and a Bratwurst lead to a fine of 10,000 euros. These two real damage events from the exali files show how the cases are connected and why even experienced agencies can fall into traps when it comes to advertising.

02.12.2022
Tips for Keeping Newsletter Subscribers
Prevent Unsubscribing: How to Keep Your Subscribers
Prevent newsletter unsubscribing: We show you the five most common reasons subscribers unsubscribe from newsletters and how you can still change their mind.

25.11.2022
Inadequate Cybersecurity
App Data Leak: How a Delivery Service Slopped Up on Security
Gorillas is a Germany delivery service where customers can use an app to do their grocery shopping. A German IT research collective discovered the startup had a massive data security problem...

21.11.2022
Make the Most of Content Cooperations
Content Collaborations: Opportunities and Risks for Site Operators and Bloggers
There are only winners in a successful content collaboration. We tell you how to find the right guest author, what to consider when writing for others and what liability risks you should keep in mind.

18.11.2022
Real Damage Event of a Headhunter
145,000 Euros in Damage: Headhunter Places Chief Financial Officer with Criminal Record
A headhunter is required to pay 145,000 euros in damages because he placed a convicted Chief Financial Officer in a company. Find out more about the real damage event here and recruiter liability risks.

11.11.2022
Once Insured, Always Up to Date
How exali's Professional Indemnity Adapts to Your Business
Once insured, always up to date: Why the insurance coverage with Professional Indemnity via exali automatically adapts to changes in your business.

31.10.2022
The Downsides of Online courses
Webinar Security Risks: What Lecturers Need To Keep In Mind
Did you know that the term “webinar” is protected by trademark law and that distance selling law applies to paid e-learning offers? Find out more about the risks associated with webinars here:

24.10.2022
Stefan Köster from the Datenschutzkontor On Cyber Security
Expert Interview: Cyber Security for Companies
In an interview, Stefan Köster tells us how freelancers and small companies can also take effective cyber-security measures and how you can permanently anchor awareness of this issue among your employees.

17.10.2022
A Real Damage Event from the IT Sector
Programmer Causes Unexpected Winnings: 11.000 Euros in Damages!
A programmer caused significantly more winners in an app sweepstakes than planned. The result: 11,000 euros in damages. We tell you the outcome of this real exali damage event here.

10.10.2022
After the Project Is Before the Project
These Tips Will Help you Generate Regular Customers as your Project Comes to an End
Are you putting too much money into acquiring new customers? Why it is worth investing in existing customers and how you can make the most of the end of a project.

07.10.2022
Business Protection for Bloggers
Risks for Bloggers: Here’s How to Protect Yourself
In addition to lots of opportunities, the blogging business also offers a lot of risks that can quickly put an end to your confidence in your own business from Poland. In our latest article, we tell you how you can avoid these stumbling blocks and protect yourself appropriately.
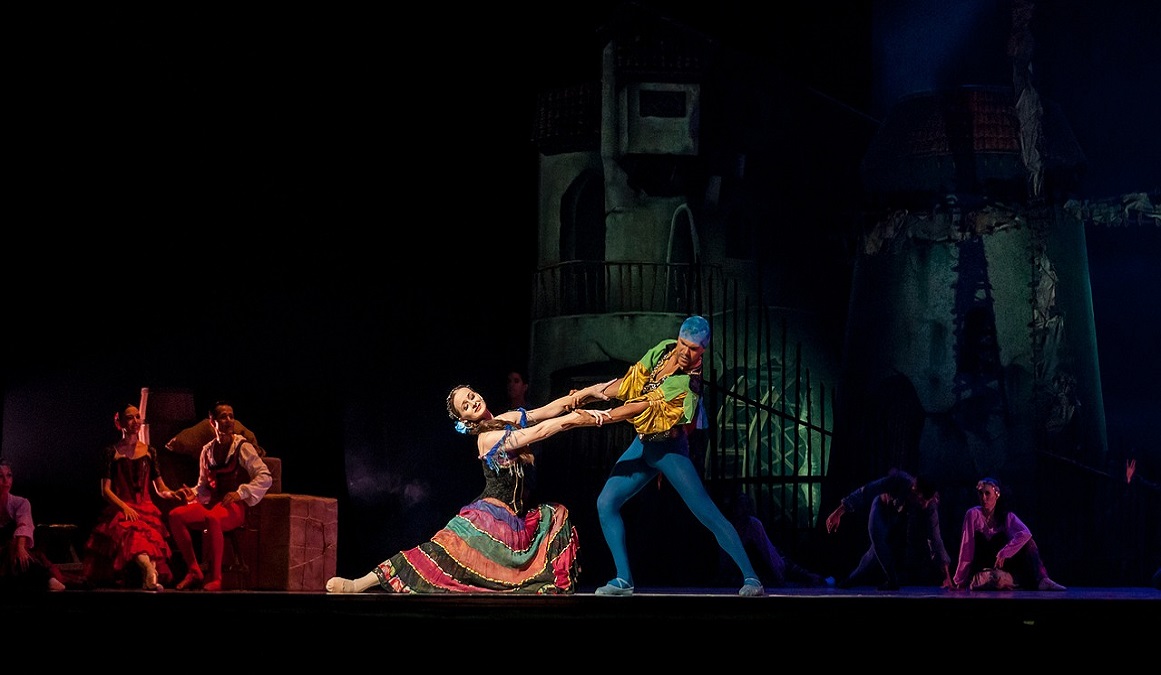
26.09.2022
IT Professionals Can Also Cause Personal Injury
Personal Injury Due to Programming Error: Singer Falls Five Meters
Due to an error made by an IT service provider, an opera singer fell five meters: Find out more about this real damage event and why personal injuries can happen in any industry...

23.09.2022
Types of Malware at a Glance
Viruses, Worms and Trojans: What Are the Differences and How You Can Protect Yourself
Virus, worm or trojan? We explain the difference between the different types of malware and how you can protect your business from expensive cyber damage.

19.09.2022
Insurance Against Data Loss
Data Loss After Security Update – a Real exali Damage Event
A routine activity turned into a nightmare for an IT service provider: When installing a security update for their client, important data disappeared – and the backup was no help. Read about this damage event to find out whether the service provider and client were able to get out of this tricky situation.

16.09.2022
80.000 Euros in Property Damage
Unintentional Emergency in Server Rooms – a Real exali Damage Event
This event kicked up a lot of dust: A company wanted to clean rented server rooms itself and triggered the extinguishing system. Cost of the damage: 80.000 euros.

09.09.2022
Destroyed Ceiling During Advertising Shoot
Customer Property Damaged During Video Shoot - a Real exali Damage Event
Expensive mistake: A media agency damaged their client’s premises while shooting a promotional video. Read here what exactly happened and who paid for the property damage in the end:

05.09.2022
Protection Against Ransomware
Ransomware Risk: How to Protect Your Business Against Becoming a Digital Hostage
Ransomware attacks are among the top threats in cybercrime. The following article tells you how you can protect your business and what you should do in the event of a successful attack.

02.09.2022
All Important Information At a Glance
Have You Received a Written Warning? This Is How You Should Respond
Written warnings have increasingly become a lucrative business model in recent years, but: Not every written warning is actually lawful. Read about who is allowed to issue a written warning and when and how to respond correctly if you receive a warning:

29.08.2022
Real exali Damage Event
Website Update Error – 90.000 Euros in Revenue Lost
Small mistake, expensive consequences: An IT service provider was supposed to make a small update on his customer’s website and accidentally took all the contact forms offline. Read about how this real damage event from the exali archives ended:



